Apicize Security
Apicize implements measures to keep your system and credentials secure when storing and executing workbooks.
Parameter At-Rest Security
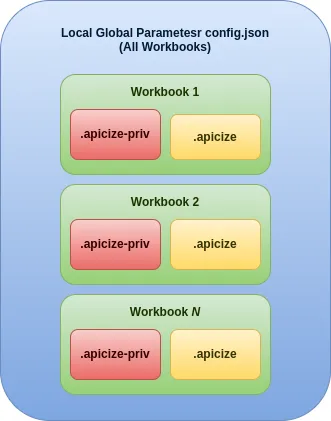
Apicize stores data in three different types of files:
- Workbook (*.apicize): Storage of requests and parameters that are intended to be shared
- Workbook Private Parameters (*.apicize-priv): Storage of parameters, specific to a workbook, such as Authorization and Certificate information, that are *not* intended to be shared
- Local Global Parameters (globals.json) Storage of parameters available for all workbooks that are *not* intended to be shared. This file is stored in your OS user's configuration directory under "/apicize"
If you want to secure parameters like Authorization and Certificates, you need to do the following:
- Specify the desired storage when defining parameters - "Workbook (Private)" or "Local Global"
- When using "Workbook (Private)" Make sure to exclude .apicize-priv from your source control configuration (ex. include this suffix in .gitignore)
Securing Test Execution
Most the time, when we run JavaScript, we are running it from within a browser or a runtime like NodeJS. It is easy to interact with browser elements (document, window) or, with NodeJS, you can access the file system and network resources.
But for an application like Apicize, arbitrary scripts can cause a security problem. What a script in a repository includes instructions to delete files, to "call home" for instructions, etc.?
The V8 engine allows execution of JavaScript in a very limited runtime environment. There is no "fs" module, nor "http", "document", etc. This greatly reduces the attack footprint of malicious test scripts.